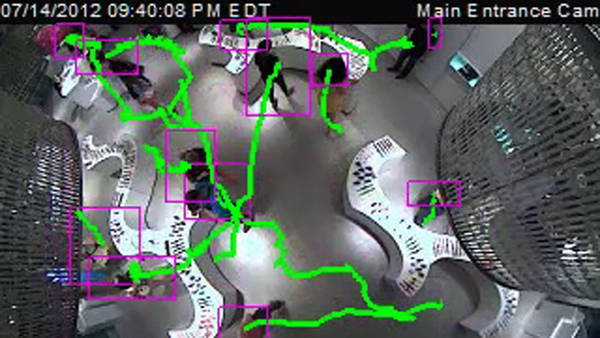
At Cyber1defense Communication, we understand the importance of tracking services for legal and ethical purposes. Our tracking services are designed to help you monitor and manage your assets, resources, and personnel in a responsible and transparent manner.
Whether you need to track the location of your vehicles, monitor the activities of your employees, or ensure the security of your premises, our tracking services provide you with the tools and technologies needed to do so effectively and ethically.
We adhere to strict legal and ethical standards in all our tracking activities, ensuring that your privacy and the privacy of others are respected at all times. Our team of experts is committed to providing you with reliable and accurate tracking information, enabling you to make informed decisions and take proactive measures to protect your assets and resources.
With Cyber1defense Communication’s tracking services, you can have peace of mind knowing that your tracking activities are conducted legally, ethically, and responsibly. Contact us today to learn more about how our tracking services can benefit your organization.