[mc4wp_form id=”2320″]
Prometei Botnet Attacking Linux Servers
-
June 20, 2025
- Posted by: Evans Asare
Prometei Botnet attacking Linux servers to mine cryptocurrency. Cybersecurity researchers have uncovered a significant resurgence of the Prometei botnet, a sophisticated malware operation targeting Linux servers for cryptocurrency mining and credential theft.
This latest campaign, observed since March 2025, demonstrates the evolving nature of cryptomining malware and its persistent threat to enterprise infrastructure worldwide.
The Prometei botnet represents a dual-threat malware family encompassing both Linux and Windows variants, designed primarily to hijack computational resources for Monero cryptocurrency mining while simultaneously stealing credentials from compromised systems.
Palo Alto Networks analysts identified this new wave of attacks in March 2025, noting significant improvements in the malware’s stealth capabilities and operational sophistication compared to previous iterations.
The botnet operates through a modular architecture that enables attackers to remotely control infected systems, deploy additional payloads, and maintain persistent access to compromised networks.
Originally discovered in July 2020 with its Windows variant taking initial precedence, the Linux version emerged in December 2020 and has since undergone continuous development.
The malware employs multiple attack vectors including brute-force credential attacks, exploitation of the notorious EternalBlue vulnerability associated with WannaCry ransomware, and manipulation of Server Message Block protocol vulnerabilities to achieve lateral movement within target networks.
This multi-pronged approach allows Prometei to rapidly expand its footprint once it gains initial access to an organization’s systems.
The financial motivation behind Prometei operations appears clear, with researchers finding no evidence linking the botnet to nation-state actors.
Instead, the campaign demonstrates characteristics consistent with profit-driven cybercriminal enterprises seeking to monetize compromised infrastructure through cryptocurrency mining while opportunistically harvesting valuable credentials for potential secondary exploitation or sale on underground markets.
The current iteration incorporates advanced evasion techniques including a domain generation algorithm for command-and-control infrastructure resilience and self-updating capabilities that enable the malware to adapt to security defenses dynamically.
These improvements make detection and mitigation significantly more challenging for traditional security solutions.
Technical Infection Mechanism and Distribution
The latest Prometei variants employ sophisticated distribution and unpacking mechanisms that significantly complicate analysis efforts.
The malware distributes itself through HTTP GET requests to a specific server located at hxxp[://]103.41.204[.]104/k.php?a=x86_64, with variations allowing dynamic ParentID assignment through the parameter hxxp[://]103.41.204[.]104/k.php?a=x86_64,.
.webp)
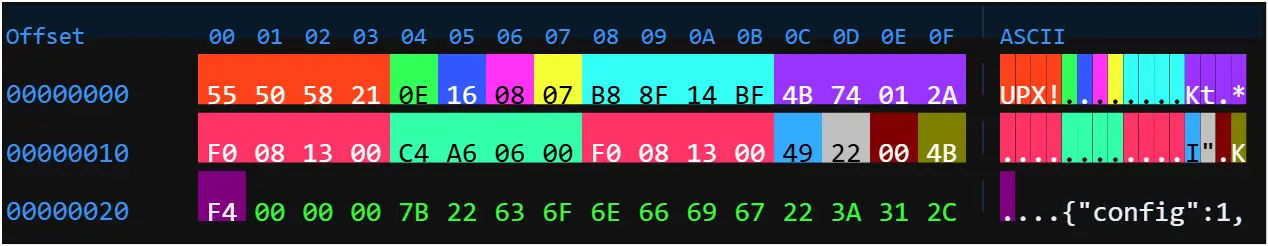
Despite the misleading .php filename, the payload consists of a 64-bit ELF executable designed specifically for Linux systems, representing a deliberate obfuscation tactic.
The malware employs Ultimate Packer for eXecutables (UPX) compression to reduce file size and complicate static analysis procedures.
However, the implementation includes a critical modification that prevents standard UPX decompression tools from functioning correctly.
The developers append a custom configuration JSON trailer to the packed executable, disrupting the UPX tool’s ability to locate essential metadata including the PackHeader and overlay_offset trailer necessary for successful decompression.
This configuration trailer contains essential operational parameters that vary between malware versions. While version two supported basic fields such as config, id, and enckey, newer versions three and four incorporate additional parameters including ParentId, ParentHostname, ParentIp, and ip fields.
These enhancements enable more sophisticated command-and-control communication and hierarchical botnet management capabilities.
Once successfully deployed, Prometei implements comprehensive system reconnaissance by collecting processor information from /proc/cpuinfo, motherboard details through dmidecode --type baseboard commands, operating system specifications from /etc/os-release or /etc/redhat-release, system uptime data, and kernel information via uname -a commands.
This intelligence gathering enables the malware to optimize its mining operations based on available hardware resources while providing attackers with detailed infrastructure mapping for potential lateral movement activities.
