[mc4wp_form id=”2320″]
Cybercriminals Exploiting Docker API Servers for SRBMiner
-
October 23, 2024
- Posted by: Evans Asare
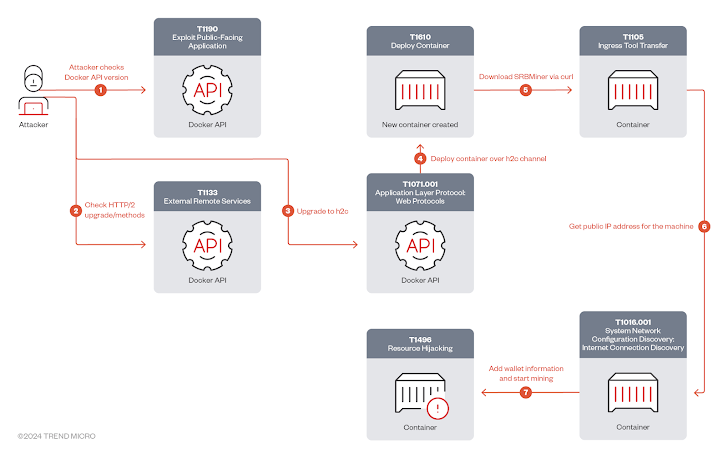
Cybercriminals exploiting docker API servers for SRBMiner crypto mining attacks. Bad actors have been observed targeting Docker remote API servers to deploy the SRBMiner crypto miner on compromised instances, according to new findings from Trend Micro.
“In this attack, the threat actor used the gRPC protocol over h2c to evade security solutions and execute their crypto mining operations on the Docker host,” researchers Abdelrahman Esmail and Sunil Bharti said in a technical report published today.
“The attacker first checked the availability and version of the Docker API, then proceeds with requests for gRPC/h2c upgrades and gRPC methods to manipulate Docker functionalities.”
It all starts with the attacker conducting a discovery process to check for public-facing Docker API hosts and the availability of HTTP/2 protocol upgrades in order to follow up with a connection upgrade request to the h2c protocol (i.e., HTTP/2 sans TLS encryption).
Read more: Kaspersky closing down its UK office.
The adversary also proceeds to check for gRPC methods that are designed to carry out various tasks pertaining to managing and operating Docker environments, including those related to health checks, file synchronization, authentication, secrets management, and SSH forwarding.
Once the server processes the connection upgrade request, a “/moby.buildkit.v1.Control/Solve” gRPC request is sent to create a container and then use it to mine the XRP cryptocurrency using the SRBMiner payload hosted on GitHub.
“The malicious actor in this case leveraged the gRPC protocol over h2c, effectively bypassing several security layers to deploy the SRBMiner crypto miner on the Docker host and mine XRP cryptocurrency illicitly,” the researchers said.
The disclosure comes as the cybersecurity company said it also observed attackers exploiting exposed Docker remote API servers to deploy the perfctl malware. The campaign entails probing for such servers, followed by creating a Docker container with the image “ubuntu:mantic-20240405” and executing a Base64-encoded payload.
The shell script, besides checking and terminating duplicate instances of itself, creates a bash script that, in turn, contains another Base64-encoded payload responsible for downloading a malicious binary that masquerades as a PHP file (“avatar.php”) and delivers a payload named httpd, echoing a report from Aqua earlier this month.
Users are recommended to secure Docker remote API servers by implementing strong access controls and authentication mechanisms to prevent unauthorized access, monitor them for any unusual activities, and implement container security best practices.

süpürge tamir uzmanı Ürün teslimi tam zamanında yapıldı. https://ai.ceo/read-blog/208021
elektrik süpürgesi servisi Güvenilir ve temiz işçilik yapıyorlar. https://woowsent.com/read-blog/555
[…] Read also: Cybercriminals Exploiting Docker API Servers for SRBMiner. […]
I went over this web site and I believe you have a lot of good information, saved to bookmarks (:.
https://www.zoritolerimol.com
Топовый игровой сайт игорный дом Лев дарит для вас великолепные опции для победных стратегий!
На онлайн-казино Лев вас радуют щедрые бонусы и огромное количество игр. Всегда здесь вы сможете выиграть огромные суммы с легкостью и удовольствием!
Площадка Лев предлагает захватывающие соревнования, которые увеличат ваш опыт игры. Примите участие в лотереях, чтобы победить.
Казино Лев гарантирует простой и удобный интерфейс, что делает игру комфортной на любом гаджете.
На Лев вас ждут не только слоты, но и игры с реальными крупье, которые обеспечат вам почувствовать себя в настоящем казино в любое время.
Кроме того, наш бонусная система предложат вам бонусные кредиты на регулярной основе.
Играй с максимумом азарта, побеждай с Лев, и получай богатства каждый день!
На сайте игрового дома Лев вас встречают удивительные акции и разнообразные игры. Именно здесь вы получите возможность завоевать невероятные призы.
Зарегистрируйтесь на игровом доме Лев и начните побеждать игровые автоматы уже моментально! казино лев, faq, правила, бонус
казино лев 2024
Sur bedandbamboo.fr vous rencontrez des outils de communication avances et une diversite de salles video. Seulement ici vous pourrez beneficier de discussions video captivantes. Inscrivez-vous sur notre site et plongez dans le chat video Coco chat deja sans delai ! Coco chat, Chatrandom, Chatrandom, Chatrandom Bonus, Coco chat, Hebergements 2025
Coco chat
Chatrandom
Chatrandom
Chatrandom