[mc4wp_form id=”2320″]
Android Telegram users hit by zero-day exploit
-
July 24, 2024
- Posted by: Evans Asare
Android Telegram users hit by zero-day exploit masquerading as “xHamster”. Telegram users find their Android phones trying to install malware named “xHamster Premium Mod.” The APK file, disguised as a media, is downloaded by the messaging app itself. Telegram released a patch to fight the complex zero-day, discovered by ESET.
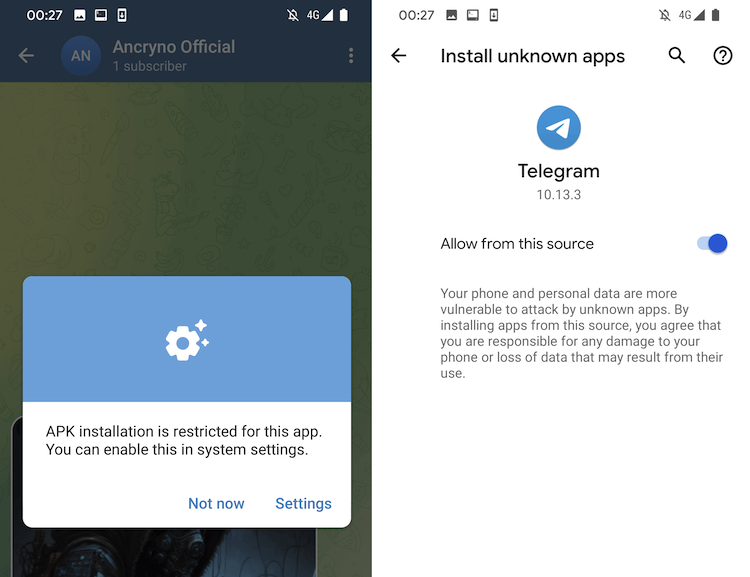
When someone sends you a video on Telegram, the media file is automatically downloaded by default. Hackers found a way to exploit that.
When a user attempts to play the video, something unexpected happens – Telegram notifies that the video is unable to play and requires a third-party app. Pressing “Open” then triggers another notification requesting permission to install unknown apps.
If the user grants that and then tries to play the video again, another prompt will pop up – to install an app called “xHamster Premium Mod.”
Multiple red flags should have arisen up until this point. However, if the user chooses to install the app, the phone will end up compromised with malware.
ESET researchers discovered that a threat actor was selling this zero-day exploit on an underground forum for an unspecified price.
“Using the exploit to abuse a vulnerability that we named EvilVideo, attackers could share malicious Android payloads via Telegram channels, groups, and chat and make them appear as multimedia files,” researchers said.
The hacker boasted that this exploit automatically downloads, bypasses security, requires one click, and supports all Telegram versions on Android.
Researchers, after analyzing the EvilVideo exploit, speculate that it abuses the Telegram API since it allows developers to upload specifically crafted files to Telegram chats or channels programmatically.
That allowed hackers and cyber crooks to create a payload, disguising the app as a multimedia preview for a 30-second video clip.
“By default, media files received via Telegram are set to download automatically. This means that users with the option enabled will automatically download the malicious payload once they open the conversation where it was shared. The option can be disabled manually – in that case, the payload can still be downloaded by tapping the download button,” researchers explain.
ESET was unable to obtain the actual payload, only the sample shared by the seller. Researchers tested the exploit on other platforms and confirmed that it did not work on Windows client or Telegram Web.
There is not much information about the threat actor behind EvilVideo. Previously they advertise Android Cryptor-as-a-Service, a tool design in a way to obfuscate malicious code so it cannot easily be detected.
Telegram issued an update on July 11th, 2024, and the app version 10.14.5 and later a no longer vulnerable to EvilVideo.

[…] Read also: Android Telegram users hit by zero-day exploit. […]
[…] Read also: Android Telegram users hit by zero-day exploit. […]
what does cialis cost cialis bestellen deutschland or buy tadalafil cheap online
https://maps.google.ie/url?sa=t&url=https://tadalaccess.com cialis 30 day free trial
when will teva’s generic tadalafil be available in pharmacies cialis professional and cialis using paypal in australia paypal cialis no prescription
https://tadalaccess.com/# vidalista 20 tadalafil tablets
cialis prescription cost: Tadal Access – cialis copay card
cialis otc switch tadalafil review or tadalafil citrate research chemical
https://maps.google.iq/url?q=https://tadalaccess.com cialis buy australia online
does cialis make you harder cialis a domicilio new jersey and cialis and alcohol safest and most reliable pharmacy to buy cialis
cialis super active plus: cialis 20mg for sale – cialis testimonials