[mc4wp_form id=”2320″]
Malicious Android Apps Posing as Google Instagram And Others.
-
May 10, 2024
- Posted by: Evans Asare
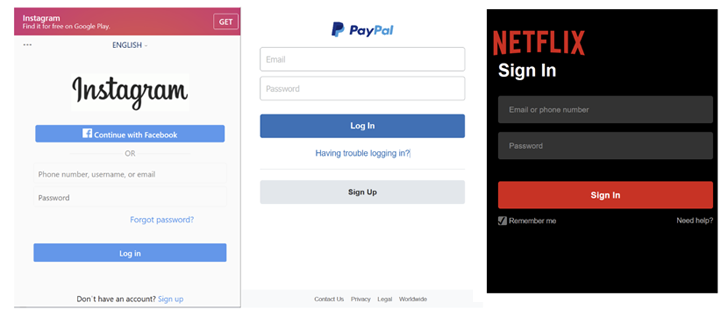
Malicious Android apps posing as Google, Instagram, and others.
Malicious Android apps masquerading as Google, Instagram, Snapchat, WhatsApp, and X (formerly Twitter) have been observed to steal users’ credentials from compromised devices.
“This malware uses famous Android app icons to mislead users and trick victims into installing the malicious app on their devices,” the SonicWall Capture Labs threat research team said in a recent report.
The distribution vector for the campaign is currently unclear. However, once the app is installed on the users’ phones, it requests that to grant it permissions to access the accessibility services and the device administrator API, a now-deprecated feature that provides device administration features at the system level.
Obtaining these permissions allows the rogue app to gain control over the device, making it possible to carry out arbitrary actions ranging from data theft to malware deployment without the victims’ knowledge.
The problems:
The malware is designed to establish connections with a command-and-control (C2) server to receive commands for execution, allowing it to access contact lists, SMS messages, call logs, the list of installed apps; send SMS messages; open phishing pages on the web browser, and toggle the camera flashlight.
The phishing URLs mimic the login pages of well-known services like Facebook, GitHub, Instagram, LinkedIn, Microsoft, Netflix, PayPal, Proton Mail, Snapchat, Tumblr, X, WordPress, and Yahoo.
The development comes as Broadcom-owned Symantec warned of a social engineering campaign that employs WhatsApp as a delivery vector to propagate a new Android malware by posing as a defense-related application.
“Upon successful delivery, the application would install itself under the guise of a Contacts application,” Symantec said. “Upon execution, the app would request permissions for SMS, Contacts, Storage, and Telephone and subsequently remove itself from view.”
It also follows the discovery of malware campaigns distributing Android banking trojans like Coper, which is capable of harvesting sensitive information and displaying fake window overlays, deceiving users into unknowingly surrendering their credentials.
The severity of it:
Last week, Finland’s National Cyber Security Centre (NCSC-FI) revealed that smishing messages are being used to direct users to Android malware that steals banking data.
The attack chain leverages a technique called telephone-oriented attack delivery (TOAD), wherein the SMS messages urge the recipients to call a number in connection with a debt collection claim.
Once the call is made, the scammer on the other end informs the victim that the message is fraudulent and that they should install an antivirus app on their phone for protection.
They also instruct the caller to click on a link sent in a second text message to install the purported security software, but in reality, is malware engineered to steal online banking account credentials and ultimately perform unauthorized fund transfers.
While the exact Android malware strain used in the attack was not identified by NCSC-FI, it’s suspected to be Vultr, which was detailed by NCC Group early last month as leveraging a virtually identical process to infiltrate devices.
Other malicious app discovered:
Android-based malware such as Tambir and Dwphon have also been detected in the wild in recent months with various device gathering features, with the latter targeting mobile phones by Chinese handset makers and primarily intended for the Russian market.
“Dwphon comes as a component of the system update application and exhibits many characteristics of pre-installed Android malware,” Kaspersky said.
“The exact infection path is unclear, but there is an assumption that the infected application was incorporated into the firmware as a result of a possible supply chain attack.”
Telemetry data analyzed by the Russian cybersecurity firm shows that the number of Android users attacked by banking malware increased by 32% compared to the previous year, jumping from 57,219 to 75,521. A majority of the infections have been reported in Turkey, Saudi Arabia, Spain, Switzerland, and India.
“Although the number of users affected by PC banking malware continues to decline, […] the year 2023 saw the number of users encountering mobile banking Trojans increase significantly,” Kaspersky noted.
Now reading: Malicious Android Apps Posing as Google Instagram And Others.

thanks for the update
[…] Must read also: Malicious Android Apps Posing as Google Instagram And Others. […]
Hello there, just became alert to your blog through Google, and
found that it is truly informative. I am going to watch out for brussels.
I’ll be grateful if you continue this in future.
Numerous people will be benefited from your writing.
Cheers!
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Your article helped me a lot, is there any more related content? Thanks!
Your article helped me a lot, is there any more related content? Thanks!
canadian online pharmacy no prescription cialis dapoxetine TadalAccess cialis 5 mg price
https://tadalaccess.com/# cialis 5mg daily how long before it works
cialis dose cialis what is it or cialis prices
http://images.google.ne/url?q=http://tadalaccess.com wallmart cialis
no prescription tadalafil cialis overdose and cialis canadian pharmacy cialis generic overnite
cialis how does it work: cialis patent expiration date – what is cialis tadalafil used for
ordering tadalafil online cialis from mexico or cialis patent
https://images.google.gg/url?sa=t&url=https://tadalaccess.com where to buy cialis over the counter
purchasing cialis online mambo 36 tadalafil 20 mg reviews and cialis 20 mg price walmart cialis is for daily use
cialis pills: TadalAccess – cialis price costco